Web application penetration testing is a vital aspect of keeping web applications secure as it exposes specific vulnerabilities through simulated attacks. This methodology evaluates a series of web application types, including SPAs, server-rendered applications, and APIs. The primary purpose is to uncover potential vulnerabilities before cybercriminals exploit them.
This testing technique plays a critical role in protecting sensitive data, including session information, user databases, and backend systems, from unauthorized access. Through simulated attacks, organizations can locate shortcomings in their web apps, helping prevent data breaches.

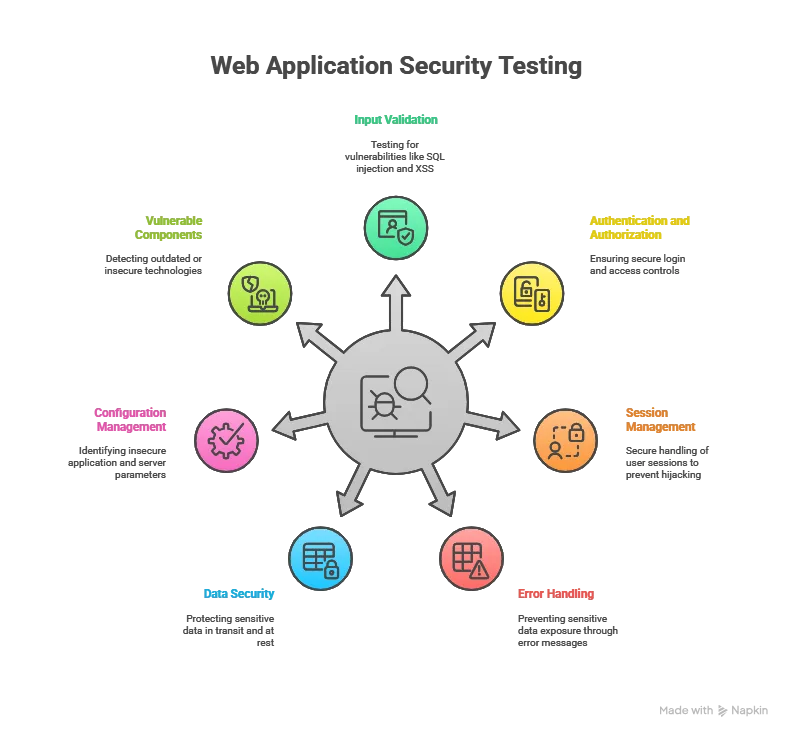
Web application penetration testing is an in-depth assessment that uncovers security flaws in a web app’s frontend, backend, APIs, and infrastructure components. It mimics real-world attack scenarios to identify both common and advanced vulnerabilities
SPAs like React or Angular, traditional server-rendered apps (PHP, ASP.NET).
REST APIs, GraphQL APIs, microservices, and databases (SQL/NoSQL).
Web servers (Apache, Nginx), cloud services (AWS, Azure).
Web application penetration testing helps uncover vulnerabilities before they are exploited by attackers. It prevents damage and reinforces your overall cybersecurity framework.
It supports meeting compliance standards such as GDPR, HIPAA, PCI-DSS, and ISO 27001, which often require regular penetration testing of web apps.
By revealing risks like DoS vulnerabilities, insecure APIs, or misconfigurations, web application penetration testing helps maintain service uptime and availability.
Integrating web application penetration testing into CI/CD pipelines ensures issues are caught early, saving costs and improving security throughout the software development lifecycle.
Avoiding breaches through web application penetration testing protects brand reputation and preserves customer trust.
1-
We define what needs to be tested—frontend, APIs, cloud environments—and select the appropriate method (black-box, gray-box) to align with business objectives.
2-
Mapping subdomains, endpoints, third-party services, and potential attack surfaces using tools like Nmap and Sublist3r.
3-
Analyzing source code and looking for secrets, logic flaws, or hardcoded vulnerabilities using tools like SonarQube.
4-
Executing attacks in real-time on the running application using tools like Burp Suite and OWASP ZAP.
5-
Focusing on broken object-level authorization, excessive data exposure, and rate-limiting vulnerabilities.
6-
Checking misconfigured servers, open ports, weak TLS, S3 buckets, and firewall policies.
7-
Simulating real-world exploitation to understand business impact and potential risk.
8-
Providing a full technical report with severity ratings, screenshots, and recommended fixes.
9-
After fixes are applied, we re-test the application to ensure no vulnerabilities remain.

High-level overview of risks and business impact.
Specific vulnerabilities with details, proof of concept, and severity ratings.
Step-by-step fixes for developers.
Unique risks for SPAs, CMS platforms, etc.
Links findings to OWASP Top 10, GDPR, PCI-DSS requirements.
Each service includes web application penetration testing methodologies tailored to the platform and risk level.
OSCP, OSWE, CISSP certified professionals.
Burp Suite Pro, Acunetix, SQLMap, and more.
Developer-friendly solutions with sample fixes.
Proven success with high-risk applications.
At least annually. More frequent testing is advised after major updates.
Testing is scheduled during non-peak hours. Minimal disruption expected.
Scanning is automated. Penetration testing includes manual validation and exploitation.
1–2 weeks for standard apps. More for complex systems.
NDA-signed testers, encrypted communications, secure data handling throughout.